Rusted Oracle
Event: HackTheBoo 2025 by HackTheBox
Category: REVERSE
Difficulty: Easy
Challenge Description
An ancient machine, a relic from a forgotten civilization, could be the key to defeating the Hollow King. However, the gears have ground almost to a halt. Can you restore the decrepit mechanism?
Solution
Initial Analysis
-
Open Ghidra, create a new project and open code browser
-
File -> Import File -> Import rusted_oracle -> Analyze it now, Yes -> Click Analyze -> Ok
-
Click functions, find main, and click to find it.
-
After clicking main from function tree, you will see the decompiled main function.
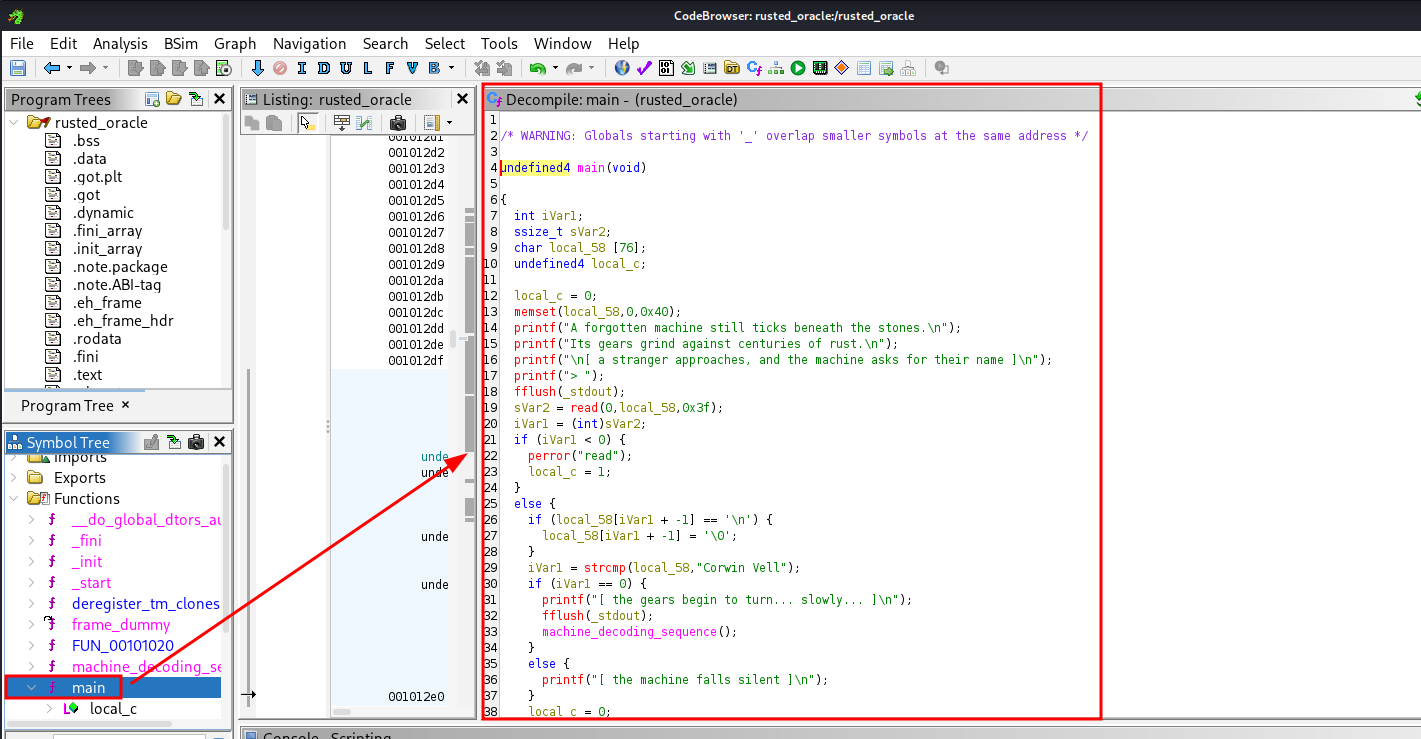
Understanding the Main Function
-
Now we take some time to understand the code, the goal is to find which part will return the flag.
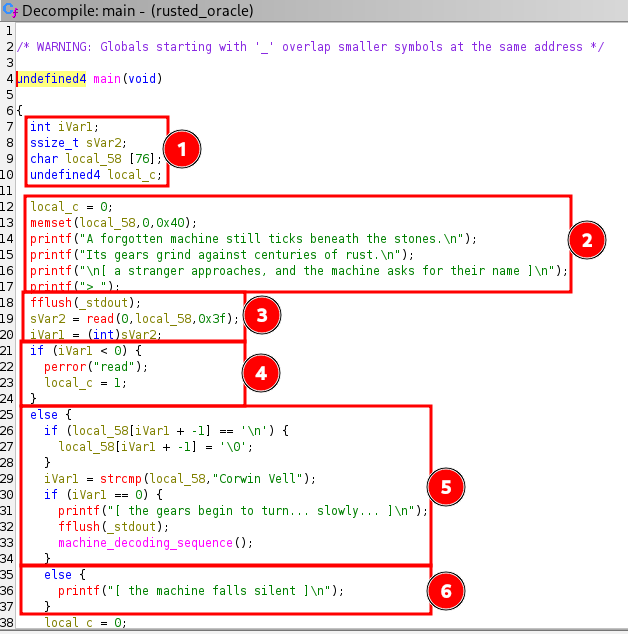
- Initialization of function variable
- Greeting message
- Input read for the name according to message and input length count
- Check for empty input
- Remove input terminator and check if input is 'Corwin Vell' which will call machine_decoding_sequence
- Fail message if the condition is not fulfilled
-
After understanding the code structure, we still cannot find the flag. Therefore we are going to investigate the function machine_decoding_sequence further. Double click on the machine_decoding_sequence.
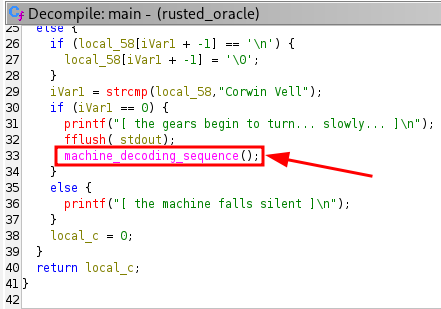
Analyzing machine_decoding_sequence Function
-
Now we try to understand the code in the machine_decoding_sequence
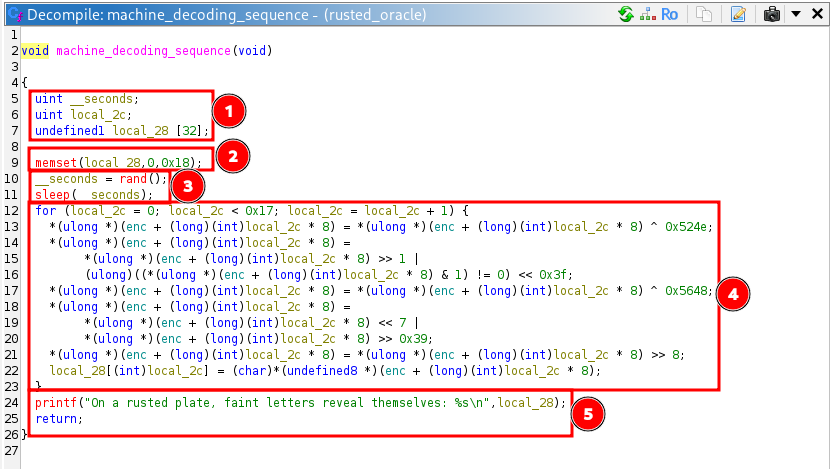
Note: When I read this code, I identify the flag first by reading from the last part first which prints the flag with a message.
- Function variable initialization, note that the local_28 have size of 32.
- Fill local_28 with 0 for the next 24 bytes (0x18)
- Sleep for a random duration
- Some XOR, shift, and rotation operation
- Print message and the value in variable local_28, I assume this is the flag.
-
So to retrieve the flag, we need machine_decoding_sequence to run and go through the operation to get back the flag in the correct form. However the sleep with random duration will prevents us from achieving the flag. How do we disable the sleep or bypass it?
Patching the Binary
-
If we select the line 10 and 11 in the decompile tab, we will see the line on the listing gets selected too. Here we try to identify what each line does.
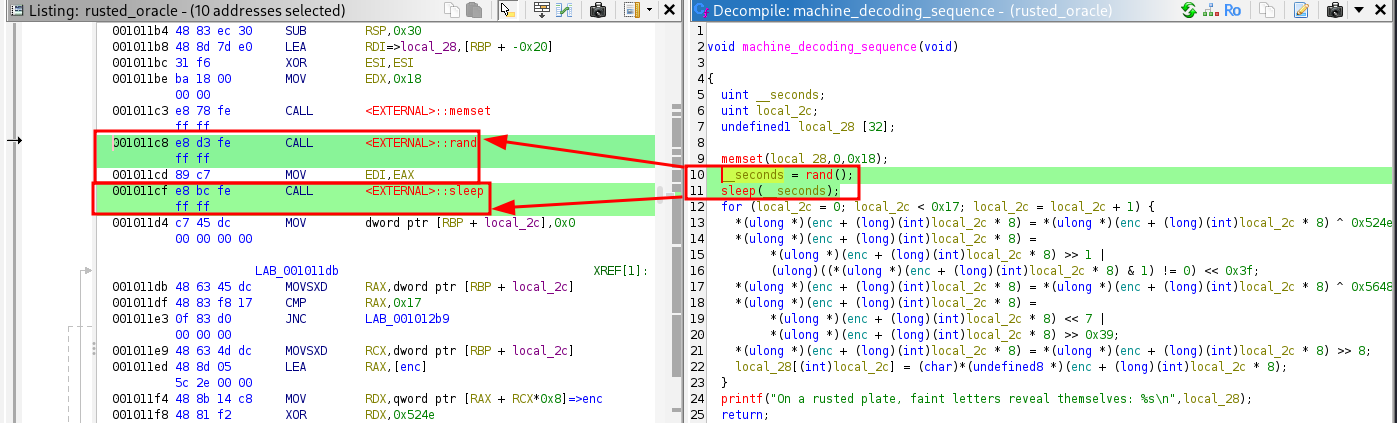
-
First it call the random function. then mov the value to be stored in the variable and last call the sleep which will fetch the value from the variable.
Extra information: MOV EDI,EAX -> copies the value from the source: (EAX register) which is the returned value of function random to destination: (EDI register) which is the variable __seconds.
-
So what if we modify the MOV instruction so that the value will not be stored? Right click on the MOV EDI,EAX line, click on patch instruction. Wait for it to finish the assemble and click ok when it mention that we got gold rating.
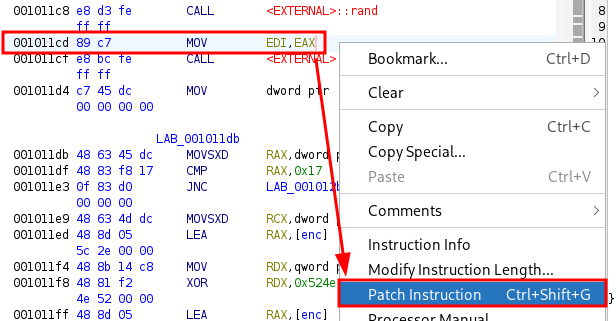
-
Repeat the step on 11, but after you clock patch instruction you will not see the assemble process. Instead you will see red box on MOV and EDI,EAX which means we can modify the instruction now.
-
After changing, you will see that the sleep function parameter is 0 and it will not sleep for random time anymore... sleep for 0 second.

Getting the Flag
-
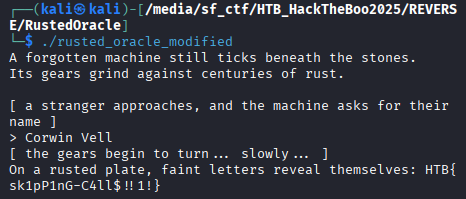
Next we export the program, export as original file.
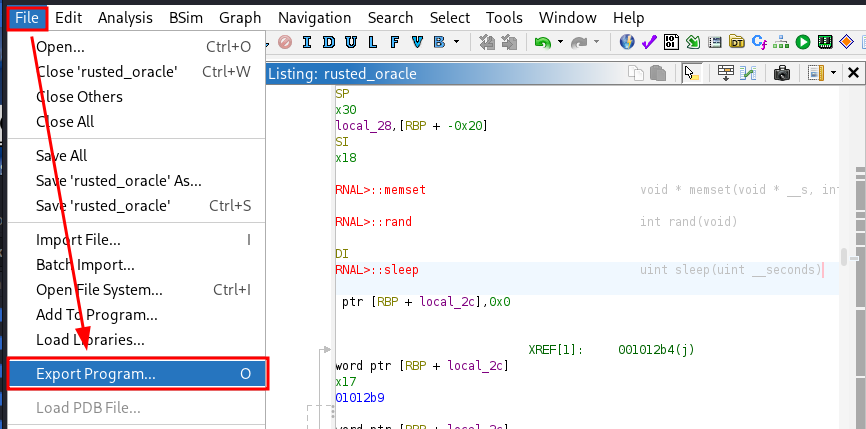
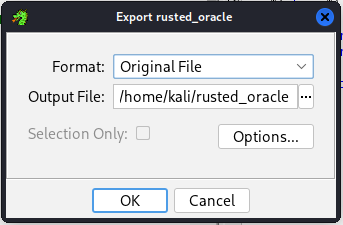
-
After exported, run the program.
-
Type Corwin Vell as input and you will find the flag.