The Azure Deception
Event: HackTheBoo 2025 by HackTheBox
Category: OSINT
Difficulty: Easy
Challenge Description
Shortly after the Door Without Handles began moving, someone sent Brynn a taunting message through the council's communication channels. It appeared to come from Microsoft's own security team—the address read azuresecuritycenter@onmicrosoft.com—but the words dripped with mockery: "It looks like you fell for it… Again. Not every onmicrosoft.com is official ;)". The domain seemed legitimate at first—onmicrosoft.com is genuine Microsoft territory—yet Brynn knows deception when she sees it. Someone is wearing a trusted mask. She must investigate this exact address through shadow-intelligence archives, identify which ghost organization has weaponized this Microsoft domain in past hauntings, and determine which named operation previously used this specific false identity to breach their victims. Even the most official-looking doors can lead to hollowed places.
Flag Format: HTB{Operation_Name}
Example (Fictional): HTB{Operation_Midnight}
Important:
- Use underscore between words
- Capitalize first letter of each word
- Include "Operation" if it's part of the name
Solution
-
The easy way to solve this is to put the challenge description inside DeepSeek with thinking and search on, then ask for it to solve by providing all of the possible answer.
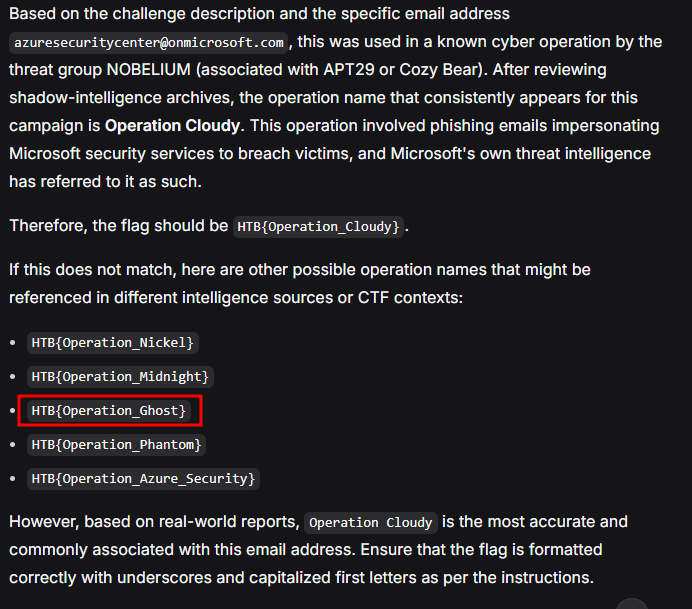
-
The harder way will be to google around with the onmicrosoft.com domain as keyword.
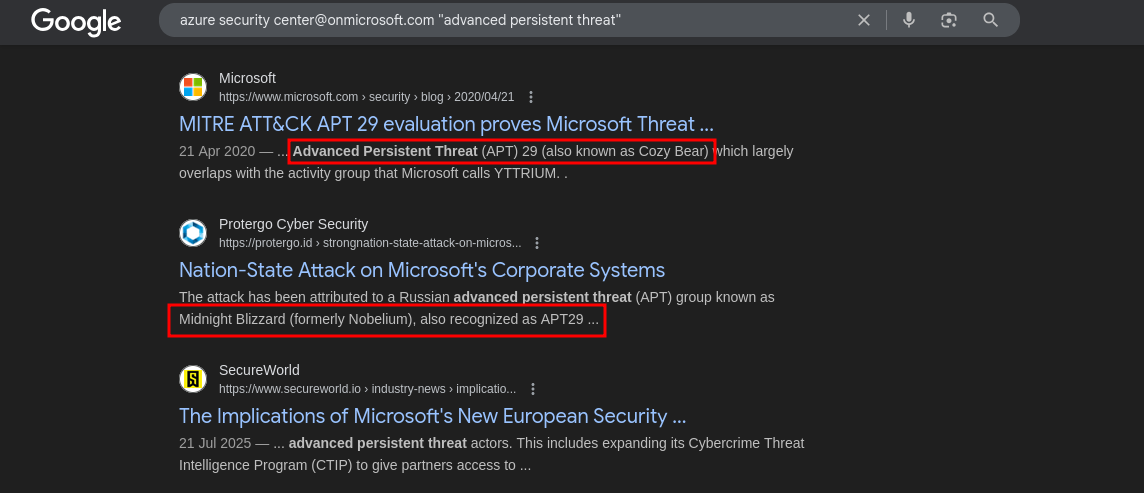
-
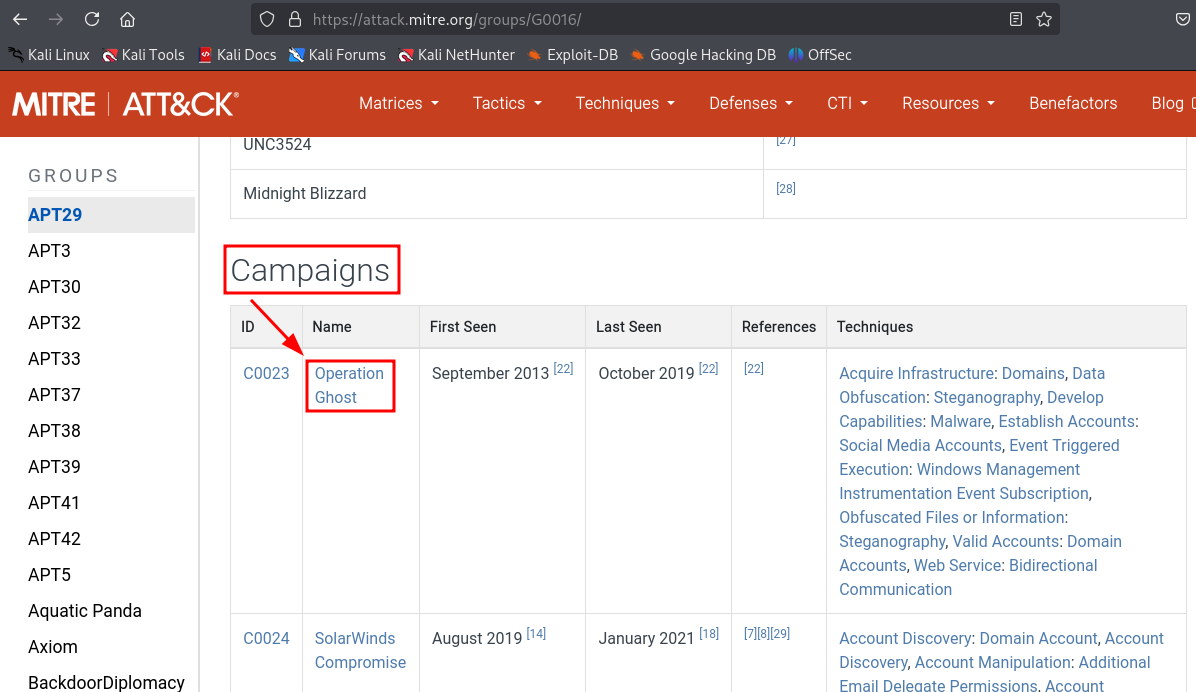
We found the APT group name, now we check around the operation done by the group.
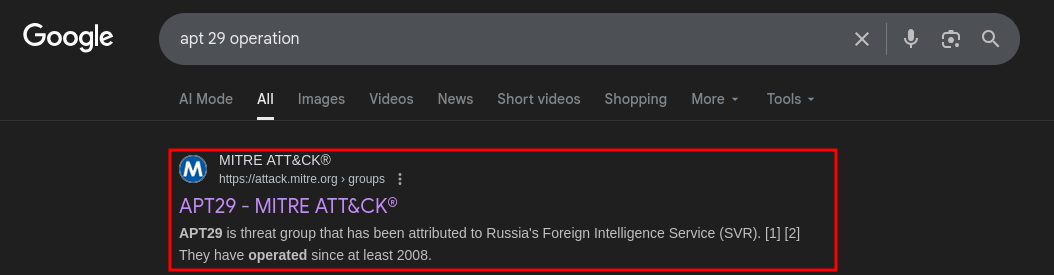
-
The first website contains the APT 29 group information.
-
Scroll down a bit and there it is, Operation Ghost.